It may seem like there are endless cybersecurity threats out there. Among them, one sounds particularly ominous—the zero-day exploit. This is when hackers crawl software to find a security flaw developers missed. In most cases, no one knows this flaw exists until it’s too late and hackers have already used the vulnerability to their advantage....
Category: Vulnerability
Hard Drive Attacks
Another group of researchers has demonstrated that hard disk drives (HDDs) can be interfered with through sound waves, but they’ve also shown that ultrasonic signals (i.e., sounds inaudible to the human ear) can be used to damage their integrity and availability. Hard Drive Attacks HDDs are non-volatile data storage devices that store and retrieve digital...
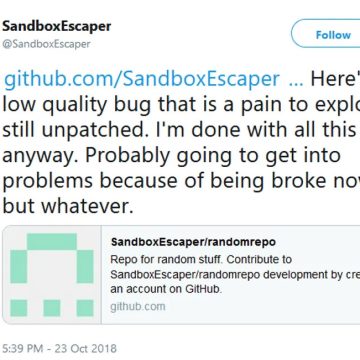
New Windows Zero-Day Exploit
Hacker Discloses New Windows Zero-Day Exploit On Twitter.A security researcher with Twitter alias SandboxEscaper has yesterday released another proof-of-concept exploit for a new Windows zero-day vulnerability. SandboxEscaper posted a link to a Github page hosting a proof-of-concept (PoC) exploit for the vulnerability that appears to be a privilege escalation flaw residing in Microsoft Data Sharing...
Github Gentoo organization hacked
Maintainers of the Gentoo Linux distribution have now revealed the impact and “root cause” of the attack that saw unknown hackers taking control of its GitHub account last week and modifying the content of its repositories and pages. The hackers not only managed to change the content in compromised repositories but also locked out Gentoo...


![20230910112229_[fpdl.in]_side-view-male-hacker-with-gloves-laptop_23-2148578161_full Github Gentoo organization hacked](https://csec.news/wp-content/uploads/2018/07/20230910112229_fpdl.in_side-view-male-hacker-with-gloves-laptop_23-2148578161_full-1-360x360.jpg)