In the interconnected world of the internet, web security is a critical concern. One of the most prevalent threats facing websites today is Cross-Site Scripting (XSS). This type of attack allows hackers to inject malicious code into trusted websites, affecting the users who interact with them. If successfully carried out, XSS attacks can hijack user sessions, steal sensitive data, and deface websites. Given how commonly these attacks occur and their potential impact, it’s vital to understand what XSS is, how it works, and—most importantly—how to protect your website from these malicious threats.
In this article, we’ll break down XSS attacks, explain how they function, the different types of attacks, and ways to defend your site from them.
What is an XSS Attack?
Cross-Site Scripting (XSS) is a vulnerability that allows cybercriminals to inject malicious scripts into web pages viewed by other users. These scripts are often written in JavaScript, and when a user interacts with the website, the injected script executes in their browser.
XSS exploits the trust users have in a specific website. By injecting harmful code into a page, attackers can trick browsers into executing that code, leading to a variety of potential consequences. These could range from stealing sensitive user data to redirecting users to malicious websites.
How Does XSS Work?
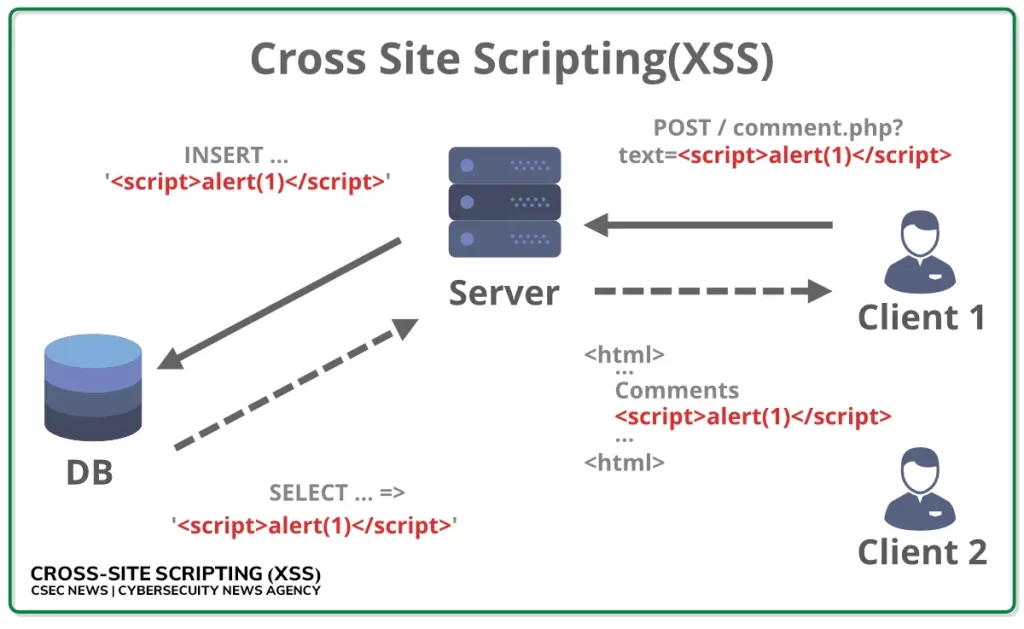
Imagine visiting a trusted website where you fill out a form, leave a comment, or simply search for something. If that website fails to properly handle user input, attackers can insert malicious scripts into the form fields or URLs. When the site displays the unfiltered content back to users, the script executes on their browser.
The key issue is that the website trusts user input without properly validating it, allowing harmful code to slip through. Here’s a simple breakdown of the process:
- Injection: An attacker sends harmful JavaScript or HTML code through a website’s input forms, comments section, or even a URL.
- Execution: The website displays the injected script back to users without proper sanitization, causing the malicious code to run.
- Impact: The injected script executes in the victim’s browser, leading to stolen data, hijacked sessions, or even malware being installed.
By exploiting a website’s failure to properly filter input, attackers can create serious damage, even though they don’t directly need to compromise the website’s server.
Types of XSS Attacks
There are three primary types of XSS attacks, each with different methods of exploiting web vulnerabilities.
Reflected XSS
In a reflected XSS attack, malicious scripts are reflected off the server and executed immediately after the victim clicks on a specially crafted link or visits a page. This type of XSS attack does not store the malicious code on the website itself but relies on it being executed when a user interacts with a malicious URL.
Example: A hacker sends a link to a user via email or social media, which contains harmful JavaScript. When the user clicks it, the script runs in their browser, stealing their session cookies or credentials.
Stored XSS
Stored XSS (also called Persistent XSS) is more dangerous because the malicious code is saved on the website’s server, usually in a database or on a content management system (CMS). Every time a user visits the affected page, the malicious script executes.
Example: A hacker posts a comment on a blog with embedded malicious JavaScript. Each time someone reads that comment, the script runs in their browser, potentially capturing sensitive data.
DOM-Based XSS
In DOM-based XSS, the attack doesn’t require the server to be involved. Instead, it happens when malicious JavaScript code is executed by manipulating the Document Object Model (DOM) in the user’s browser. The website’s JavaScript modifies the page structure based on user input, which can be exploited if not validated properly.
Example: A website dynamically updates the page using JavaScript based on URL parameters (such as search queries). If the website doesn’t properly handle these inputs, an attacker could inject malicious code through the URL, which the browser would execute.
Why Are XSS Attacks Dangerous?
XSS attacks are harmful for several reasons:
- Session Hijacking: Attackers can steal session cookies, allowing them to impersonate legitimate users and access their accounts.
- Phishing: Malicious scripts can redirect users to fake login pages or phishing websites, tricking them into entering their credentials.
- Data Theft: Sensitive information such as credit card numbers, personal details, or private messages can be stolen.
- Malware Distribution: XSS can be used to install malware on users’ devices, which can further compromise their security.
- Reputational Damage: If users are targeted by an XSS attack on a site, it could damage the website’s reputation and undermine user trust.
For both website owners and users, XSS attacks can result in significant privacy and security risks.
Real-World Examples of XSS Attacks
To truly grasp the impact of XSS, it helps to look at some real-world cases:
- Twitter (2010): A worm took advantage of XSS vulnerabilities to spread rapidly across user profiles, leading to automatic, unauthorized tweets and spam.
- Yahoo (2014): An XSS vulnerability in Yahoo Mail allowed attackers to inject malicious code that would trigger when a user opened a message, potentially compromising the user’s account.
- British Airways (2018): An attacker used XSS to inject a script into the site’s checkout process, which then captured payment details from customers as they entered them.
These cases show that even large, well-known companies aren’t immune to XSS attacks, underscoring the importance of secure coding practices.
Detecting XSS Vulnerabilities
Detecting XSS vulnerabilities is essential for securing your web applications. Here are some common ways to detect potential weaknesses:
- Manual Testing: Test input fields, forms, and URLs by submitting unusual or suspicious data to see if the website handles it properly.
- Automated Scanning: Tools like OWASP ZAP and Burp Suite scan websites for common XSS vulnerabilities and offer detailed reports.
- Penetration Testing: Hire ethical hackers to simulate attacks and uncover vulnerabilities before they can be exploited by malicious actors.
- Code Reviews: Regularly audit your codebase to identify potential vulnerabilities and ensure proper input sanitization is in place.
Best Practices to Prevent XSS Attacks
Here’s what you can do to safeguard your website from XSS attacks:
1. Sanitize User Inputs
Ensure all user inputs are sanitized to strip out potentially dangerous HTML, JavaScript, or other executable code. Never trust user-generated content. Use libraries or built-in functions to clean input data.
2. Output Encoding
Ensure that any data that is displayed on your site, whether from user input or databases, is properly encoded. This makes sure that user input is rendered as text instead of executable code.
3. Use Content Security Policy (CSP)
A CSP is a powerful tool to help mitigate the risk of XSS attacks. It specifies which content sources are trusted and which are not. For example, it can block inline scripts or restrict the loading of content from untrusted domains.
4. Use Secure Frameworks
Many modern frameworks like React and Angular have built-in protections against XSS by automatically escaping user input and reducing the risk of attacks.
5. Implement Secure HTTP Headers
Setting the right HTTP security headers, such as X-XSS-Protection, can provide an additional layer of defense by alerting browsers to block certain types of XSS attacks.
Common Tools for XSS Testing
To better understand your website’s security posture, there are several tools you can use to identify XSS vulnerabilities:
An open-source web application security scanner that can detect XSS vulnerabilities.
A comprehensive suite of tools for web security testing, including scanning for XSS.
A commercial web vulnerability scanner designed to detect XSS and other security issues.
Future Trends and the Evolution of XSS Attacks
As web applications become more complex, XSS attacks continue to evolve. For example, with the rise of Single Page Applications (SPAs) and JavaScript frameworks, DOM-based XSS attacks are becoming more prevalent. This requires developers to stay vigilant and up-to-date with new security practices and tools.
The future of XSS prevention will likely involve increased reliance on machine learning and AI to detect and prevent malicious activity in real-time.
Conclusion
XSS attacks remain one of the most significant threats to website security, but understanding how they work and adopting best practices can help protect your site and its users. From sanitizing user input to leveraging modern security tools like CSP and output encoding, taking a proactive approach is the best way to safeguard against these attacks. By staying informed and continuously testing your web applications for vulnerabilities, you can ensure that your website remains a safe space for users to visit and interact with.
In the ever-changing landscape of cybersecurity, vigilance and constant improvement are essential to keep XSS attacks at bay and maintain a secure, trusted online environment.


















